Tap to move to section
Context
Assessments & Engagements
1. User & Market Research
Interviews & Competitive Analysis
2a. Security Staff Screens
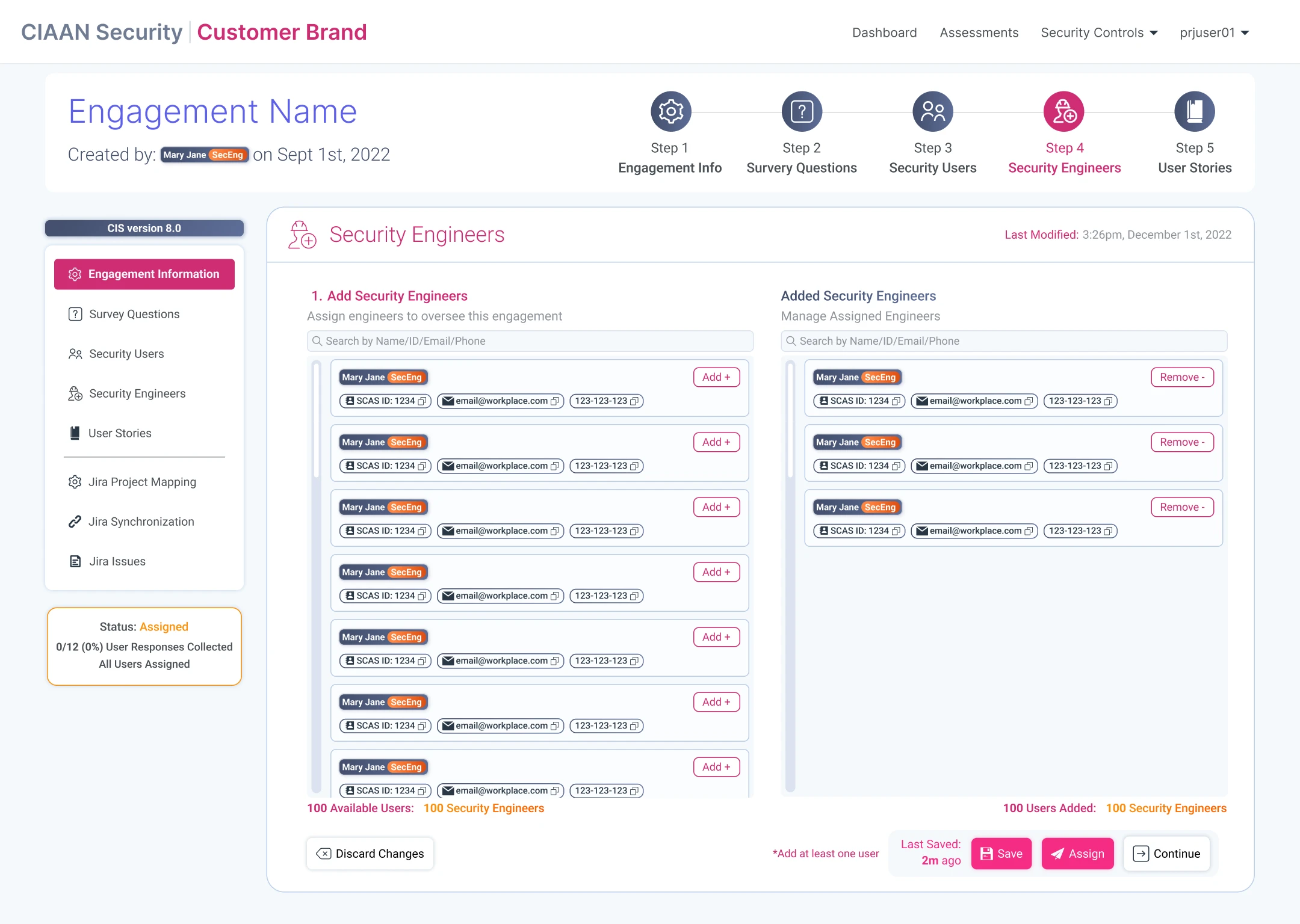
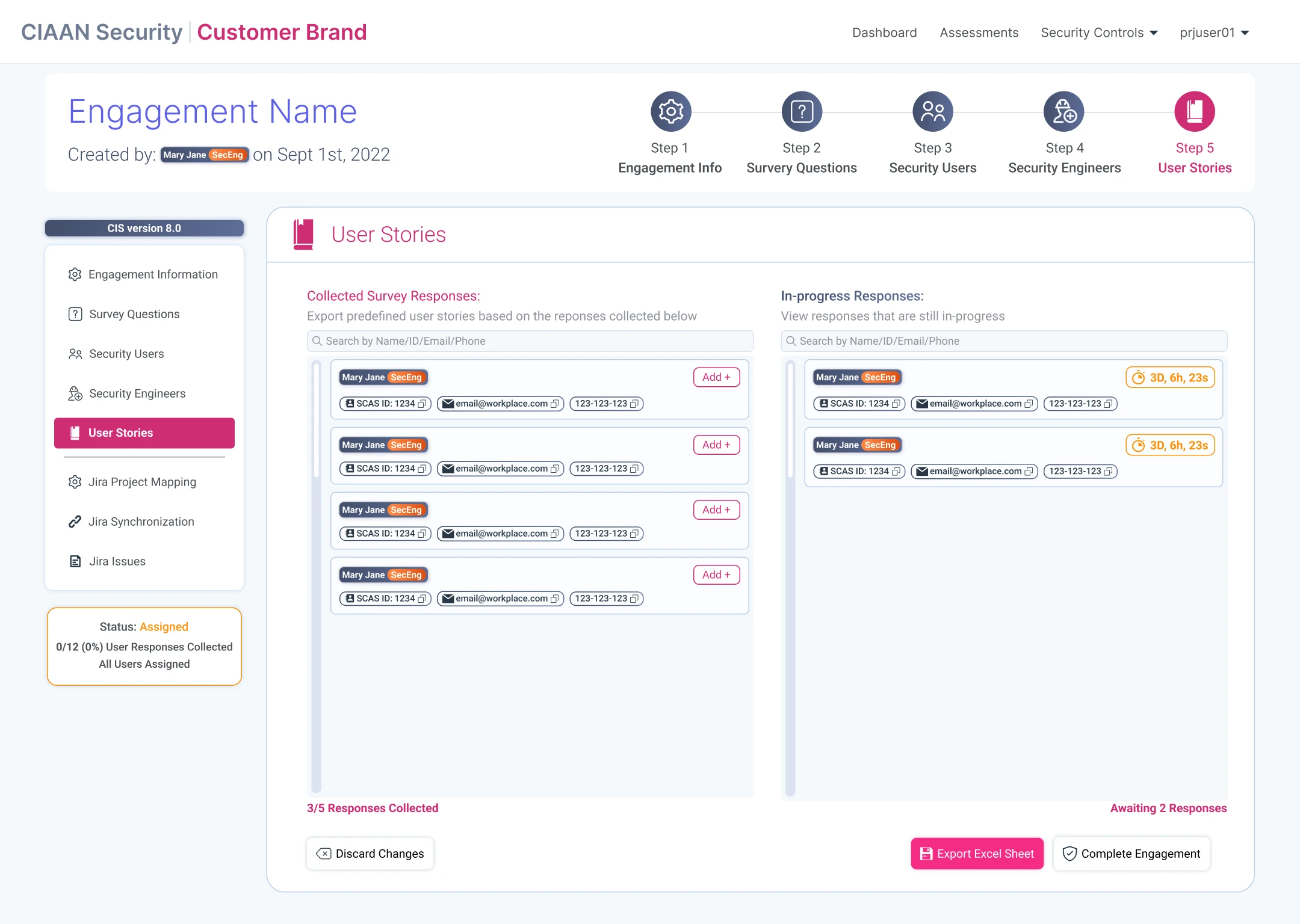
Engagements: Creation & Management
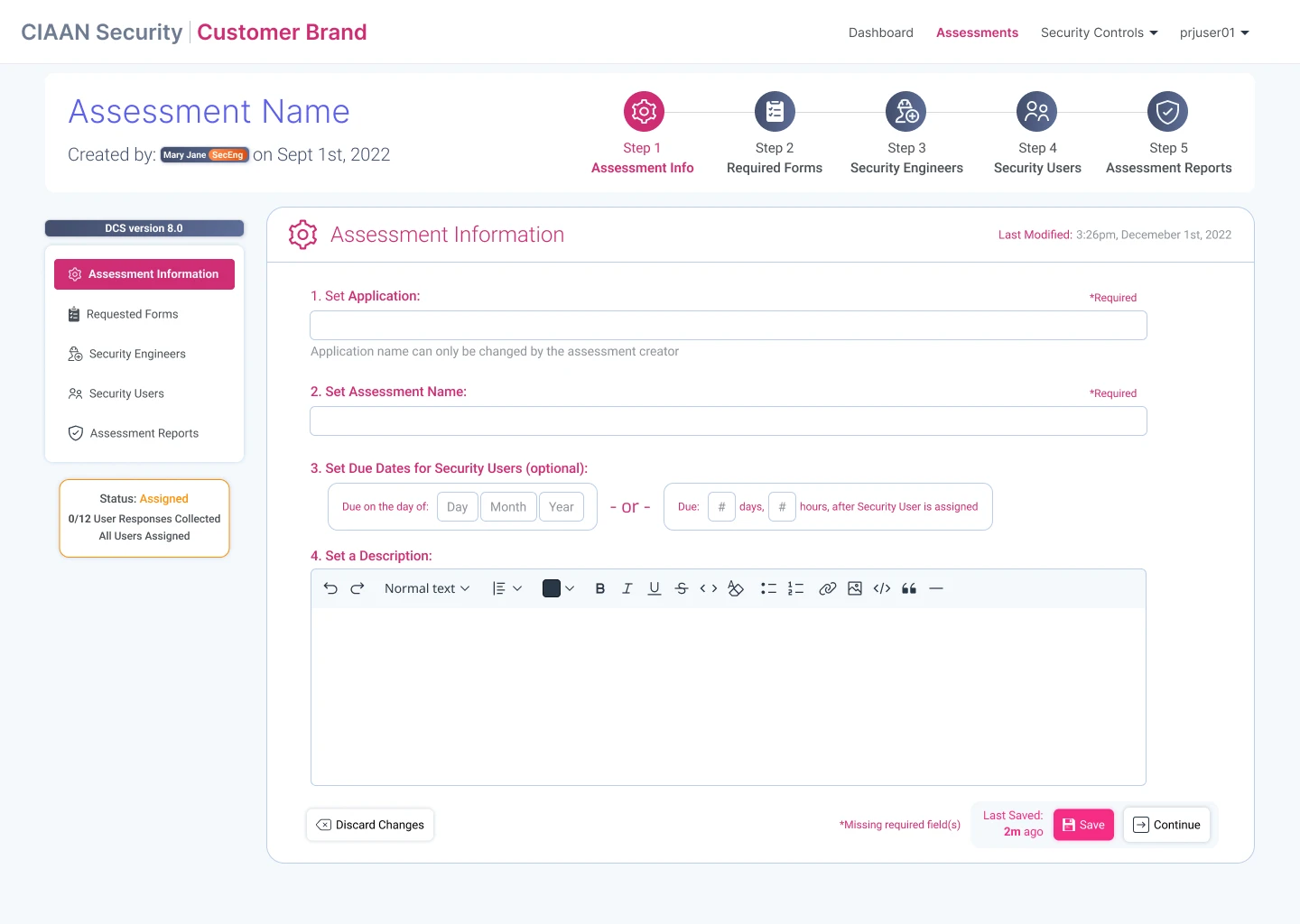
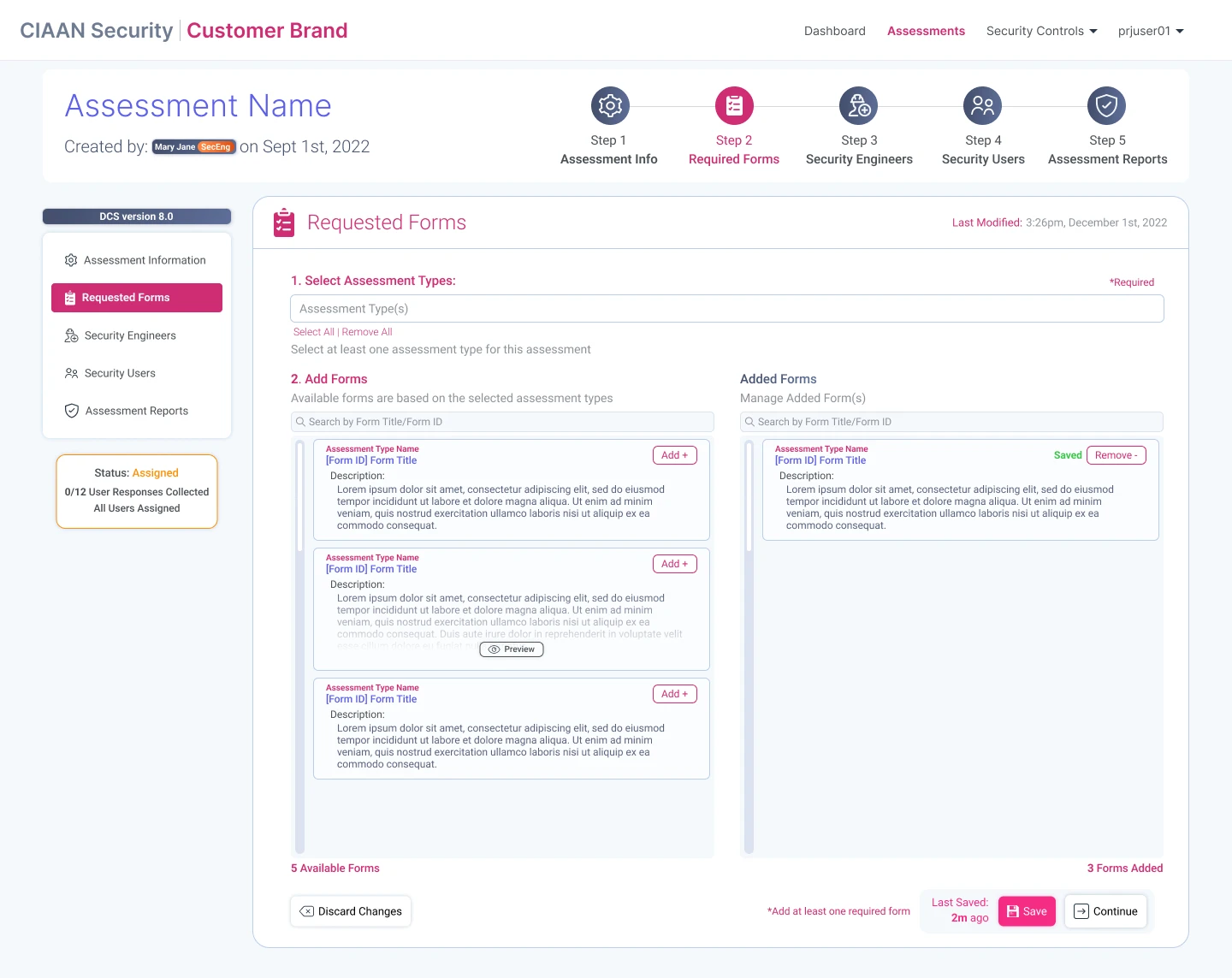
Assessments: Creation & Management
2b. Security User Screens
Assessment Form Delivery
2c. Component Library
Design System
3. User Testing
3. User Testing
That's all for now!
CIAAN Security
Cybersecurity Automation Platform Design
Background
Last Updated 19/2/2025
Project Length
August 2024 - May 2025
Project Type
Web App Product Design
Role
Sole UX/UI Designer
SCAS (Security Controls & Automation System) is a cybersecurity platform featuring a suite of security automation tools tailored for T-Mobile as bid to win a development contract against other competing software vendors. The work covered below focuses on the part of SCAS responsible for automating security assessments and engagements for T-Mobile's usecase.
CIAAN Security (Security Controls & Automation System) is a Canadian-based cybersecurity startup specifically founded to develop the SCAS platform for T-Mobile and other potential customers.
Project Background
Project Goals & Scope
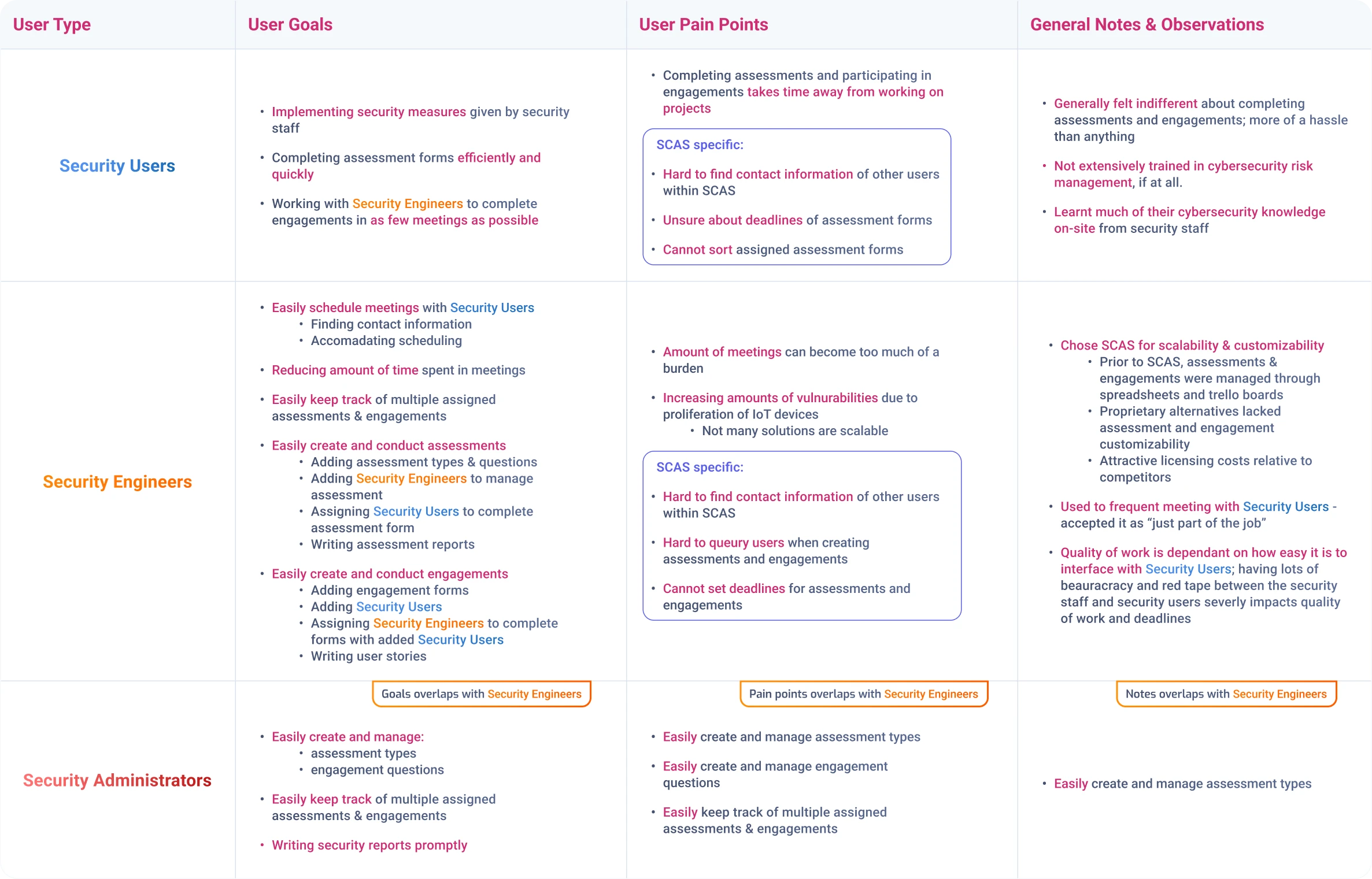
My responsibility was to research, ideate, then design a SCAS workflow to automate the creation and management of Security Assessments and Engagements to be used by both T-Mobile's cybersecurity team (Security Engineers and Administrators), as well as regular non-cybersecurity employees.
Project Stages
This project was divided in 3 stages spanning 6 weeks. Both sets of workflow screens below(2a & 2b) were worked on in tandem as deemed appropriate in-situ.
1. User & Market Research: 1 Week
Conducting expert interviews & competitive analysis to ideate Security Staff & Security User workflow design.
2a. Security Staff Screens: 4 Weeks
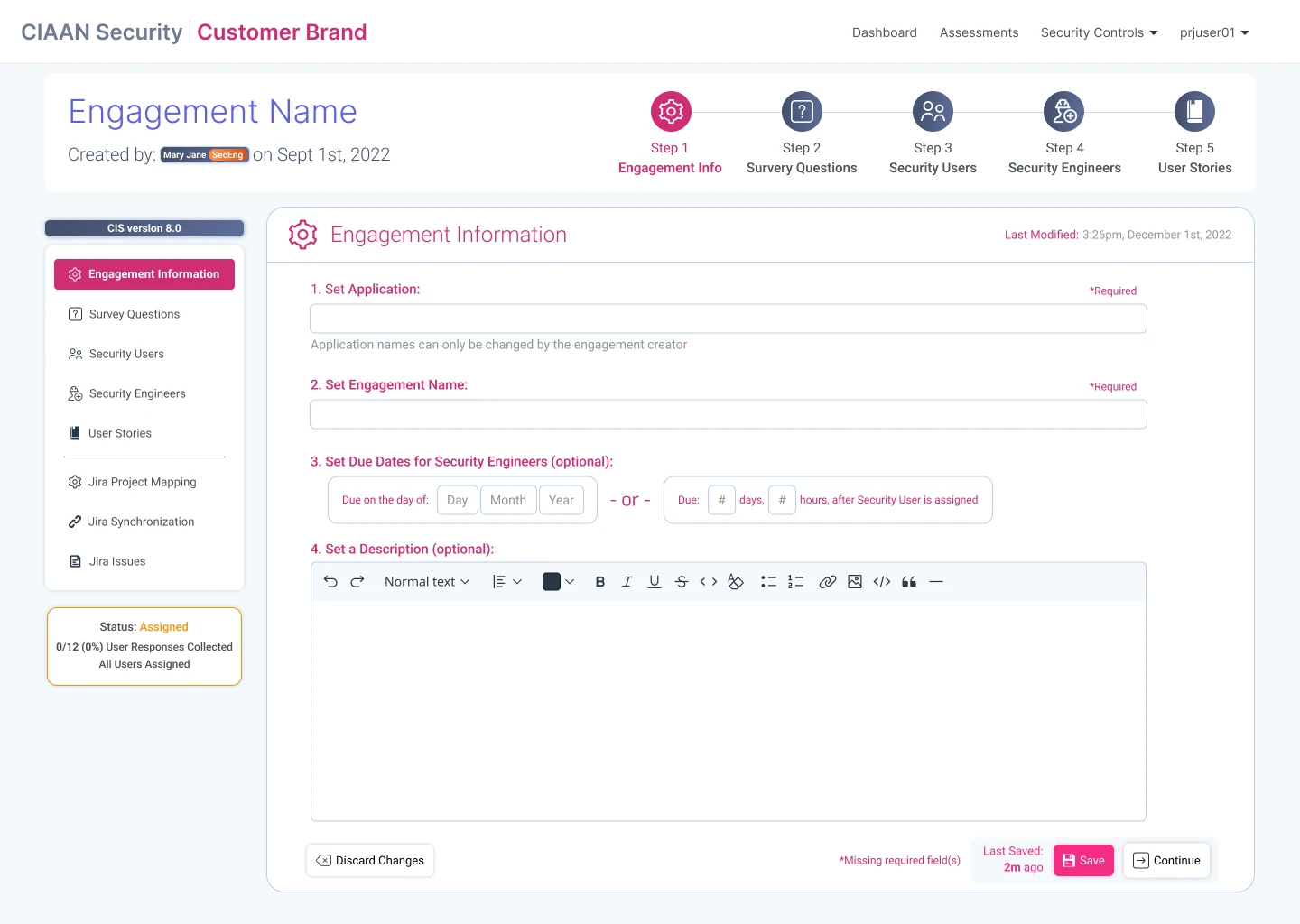
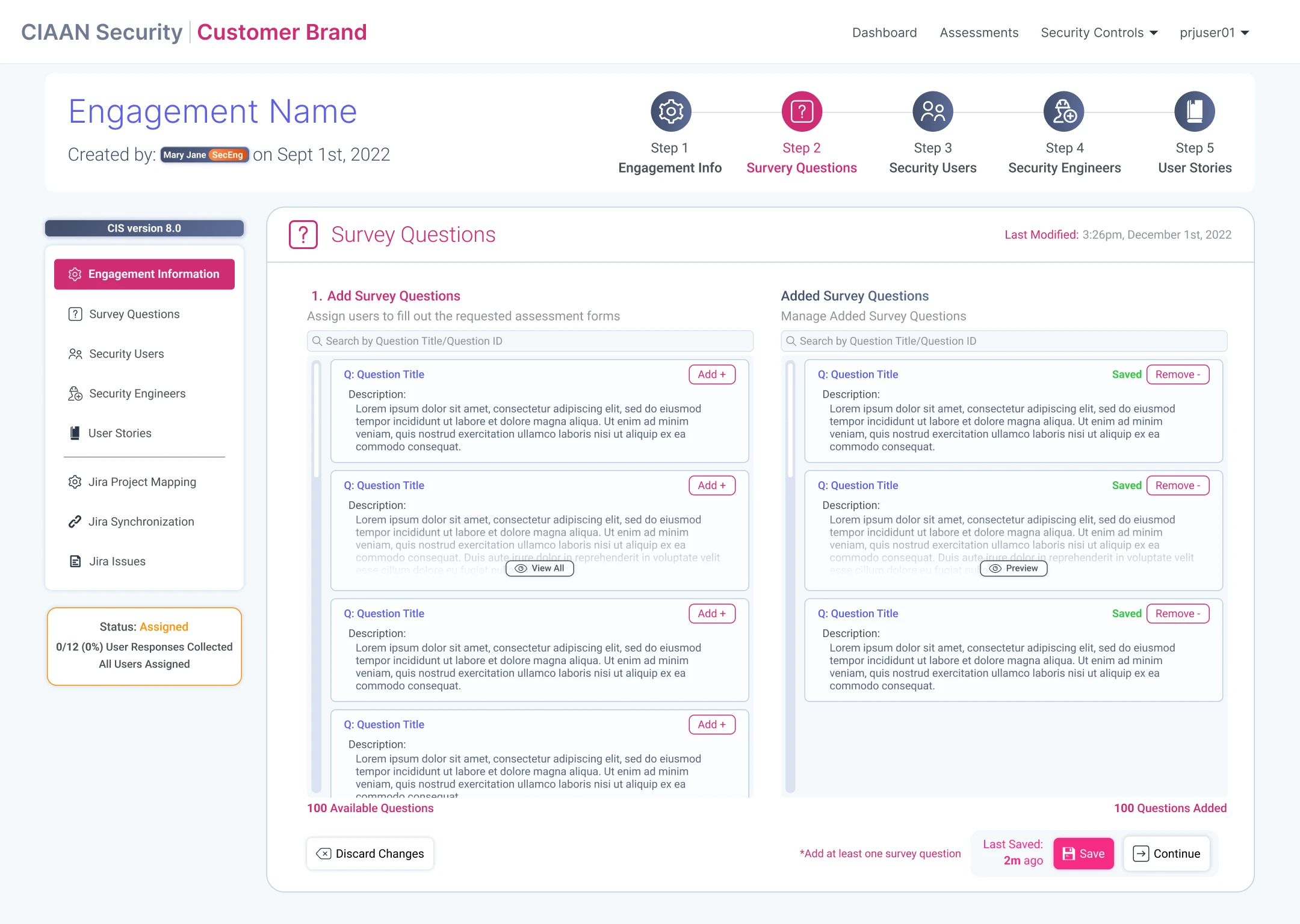
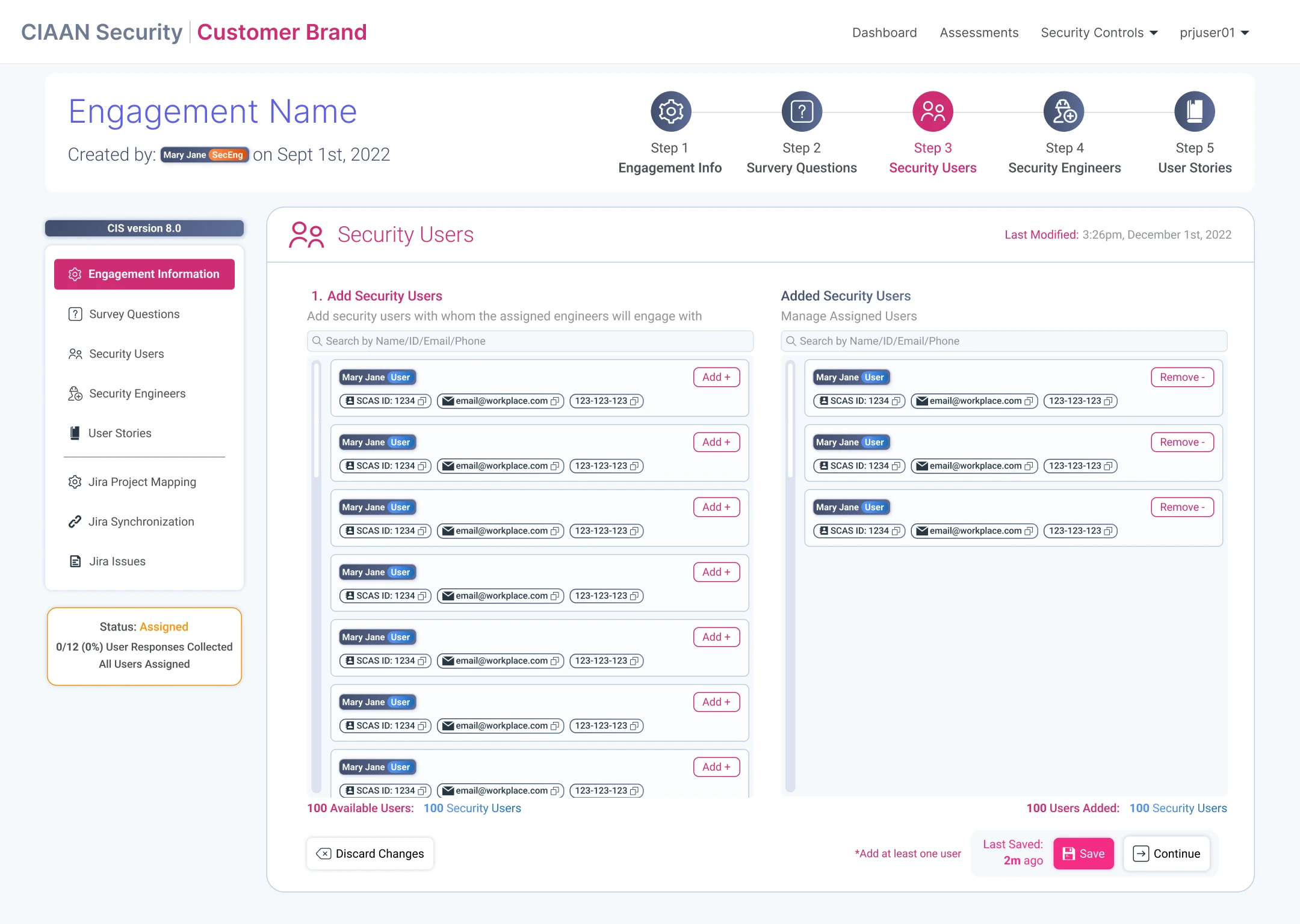
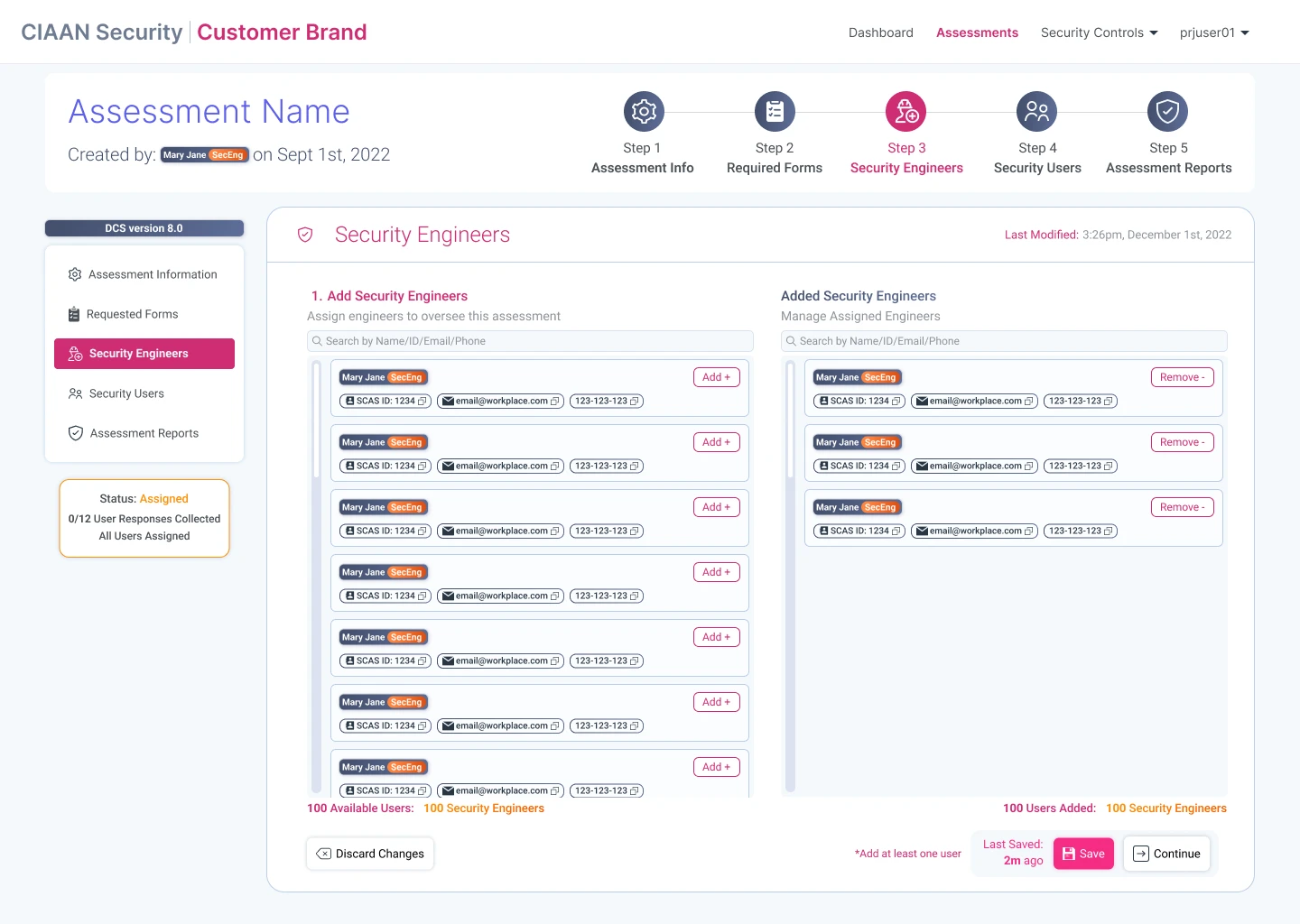
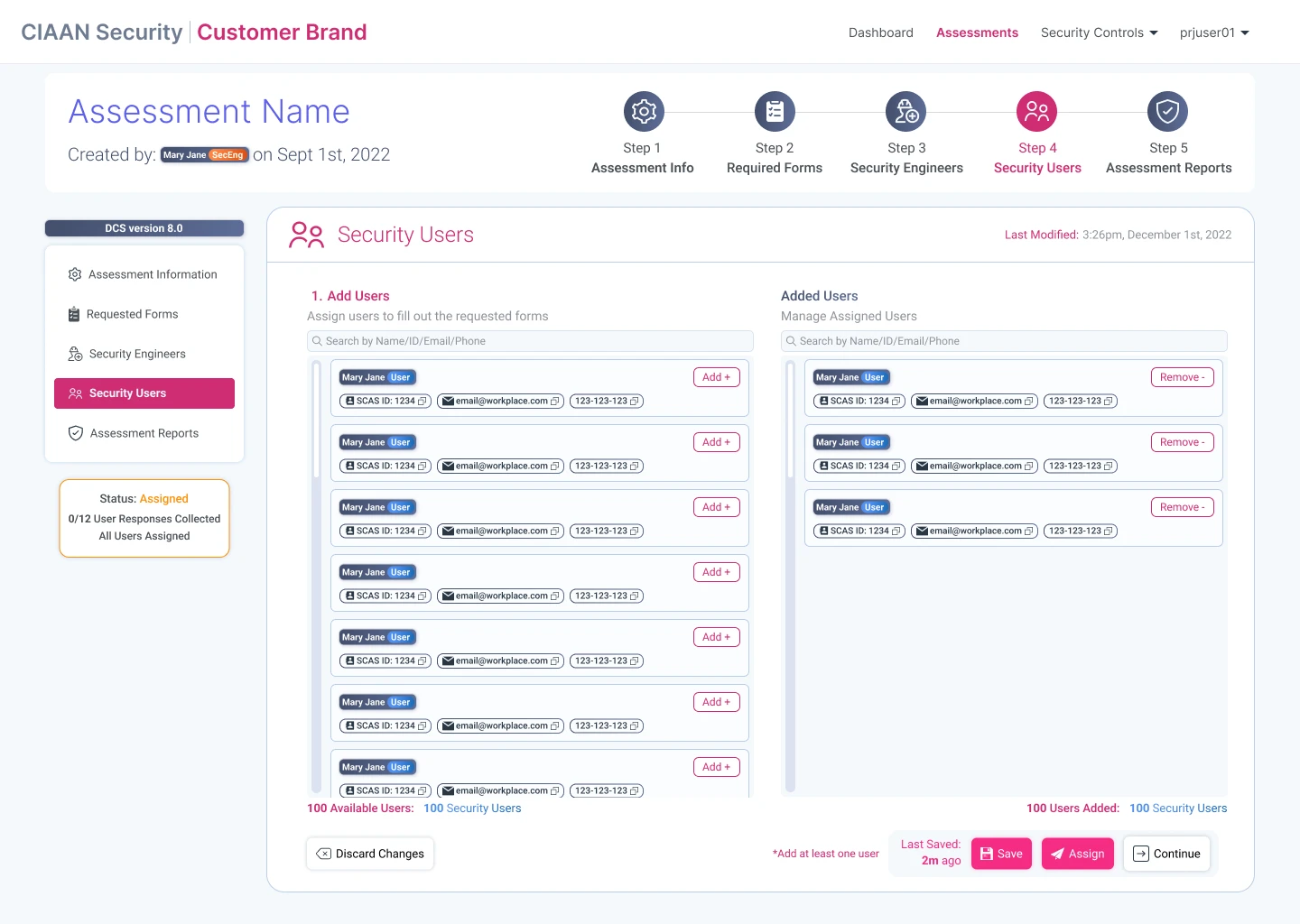
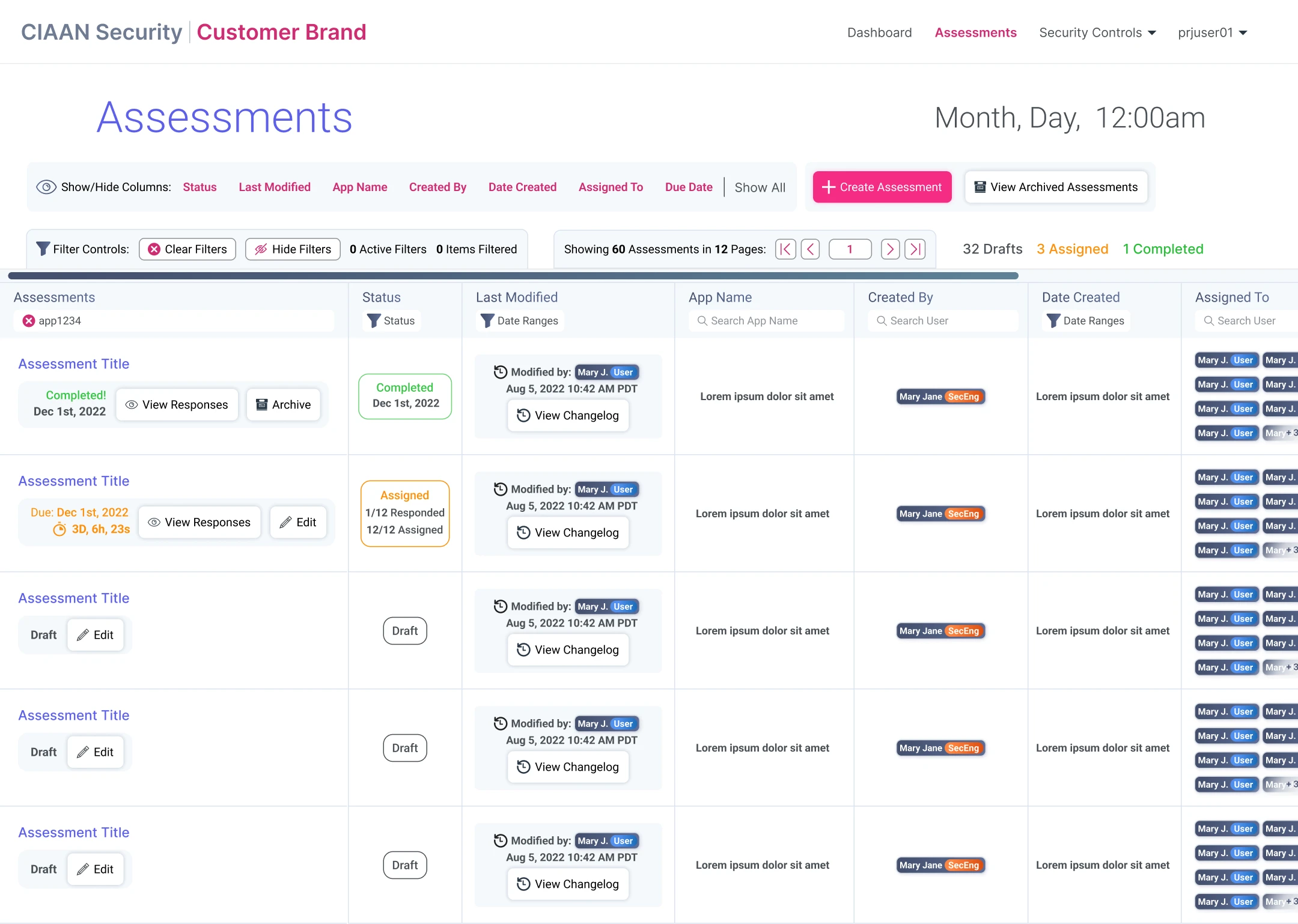
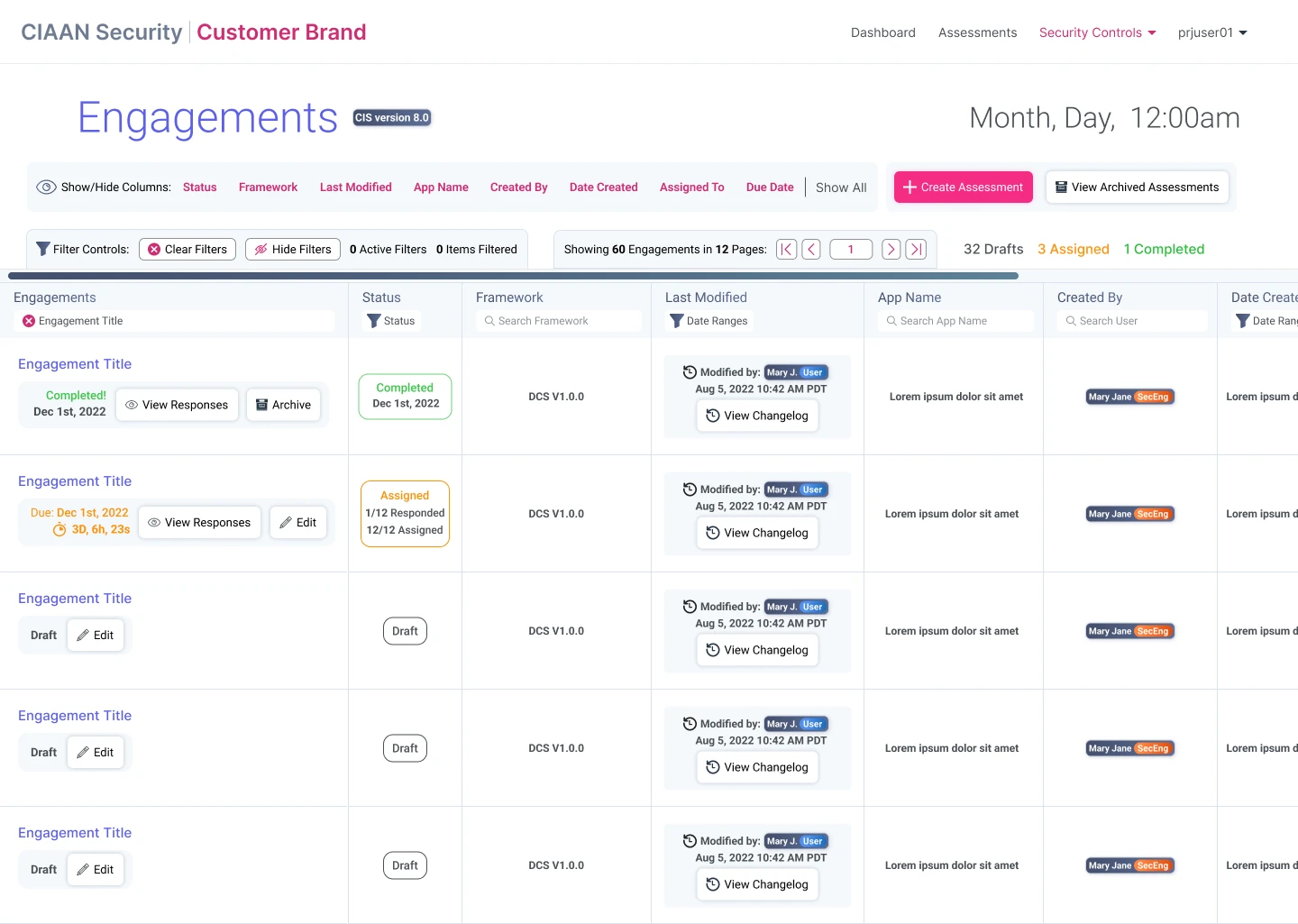
Designing the SCAS workflow for security staff to create, and manage security engagements & assessments.
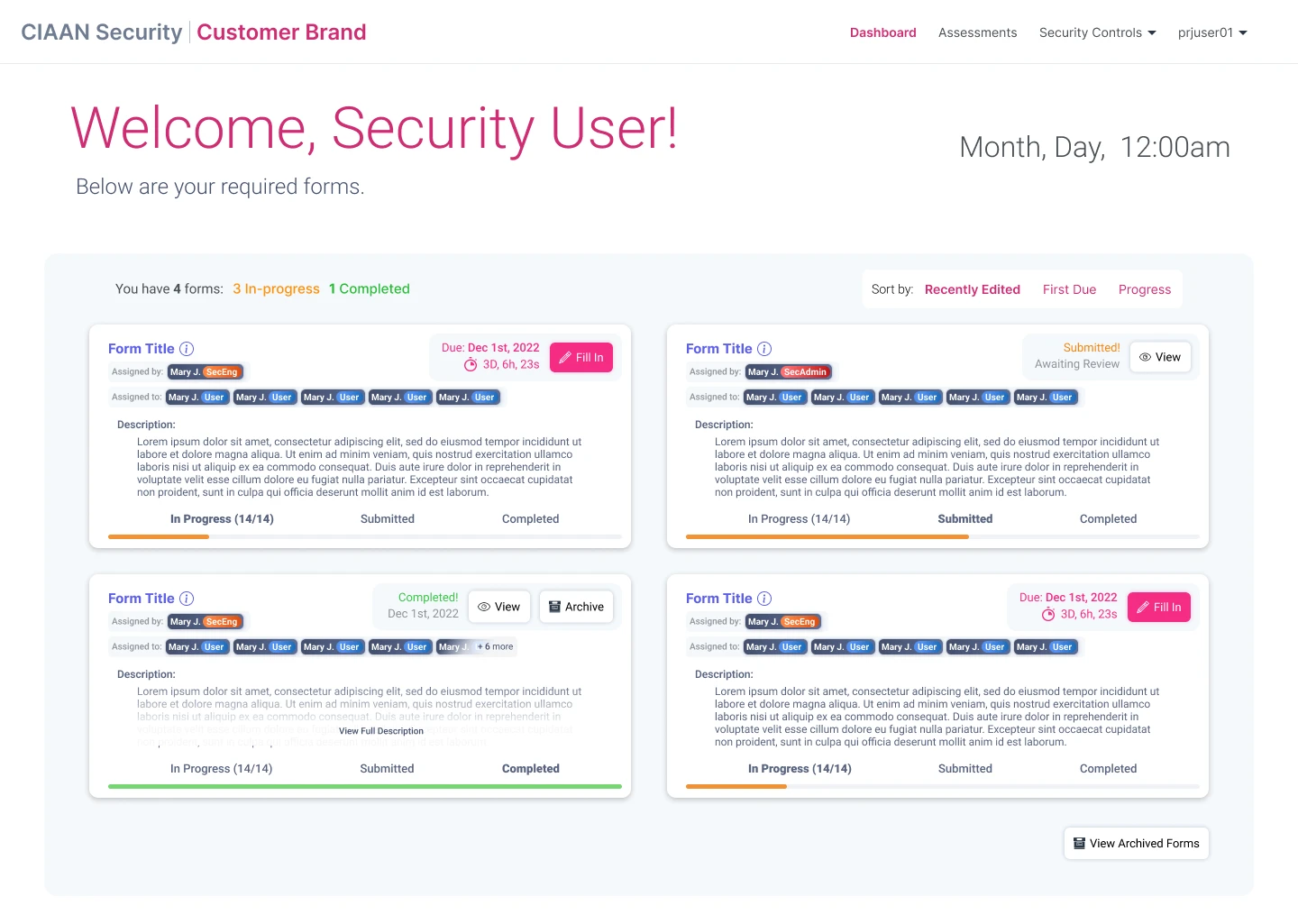
2b. Security User Screens: 1 Week
Designing the security user facing side of receiving and completing administered security assessment forms.
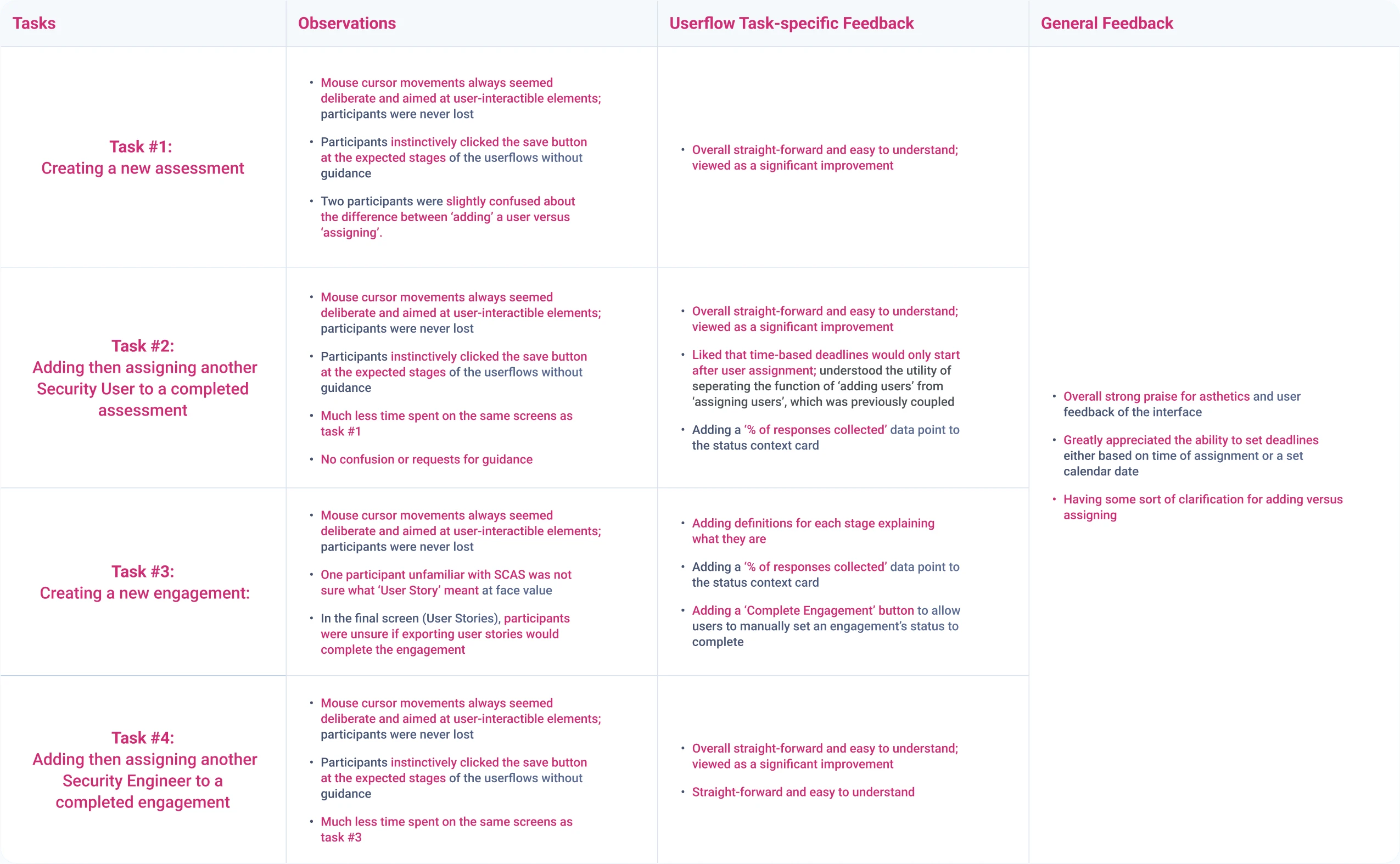
3. User Testing: 1 Week
Conducting cognitive walkthroughs using assessing the workflow for security staff in creating and managing assessments & engagements.
NOTE: For the sake of deadlines and stakeholder presentations, I opted to dive straight into high fidelity prototyping.
(For a more traditional sprint methdology please check out my Flikshop case study!)
Table of Contents
Context
Assessments & Engagements
1. User & Market Research
Interviews & Competitive Analysis
2a. Security Staff Screens
Engagements: Creation & Management
Assessments: Creation & Management
2b. Security User Screens
Assessment Form Delivery
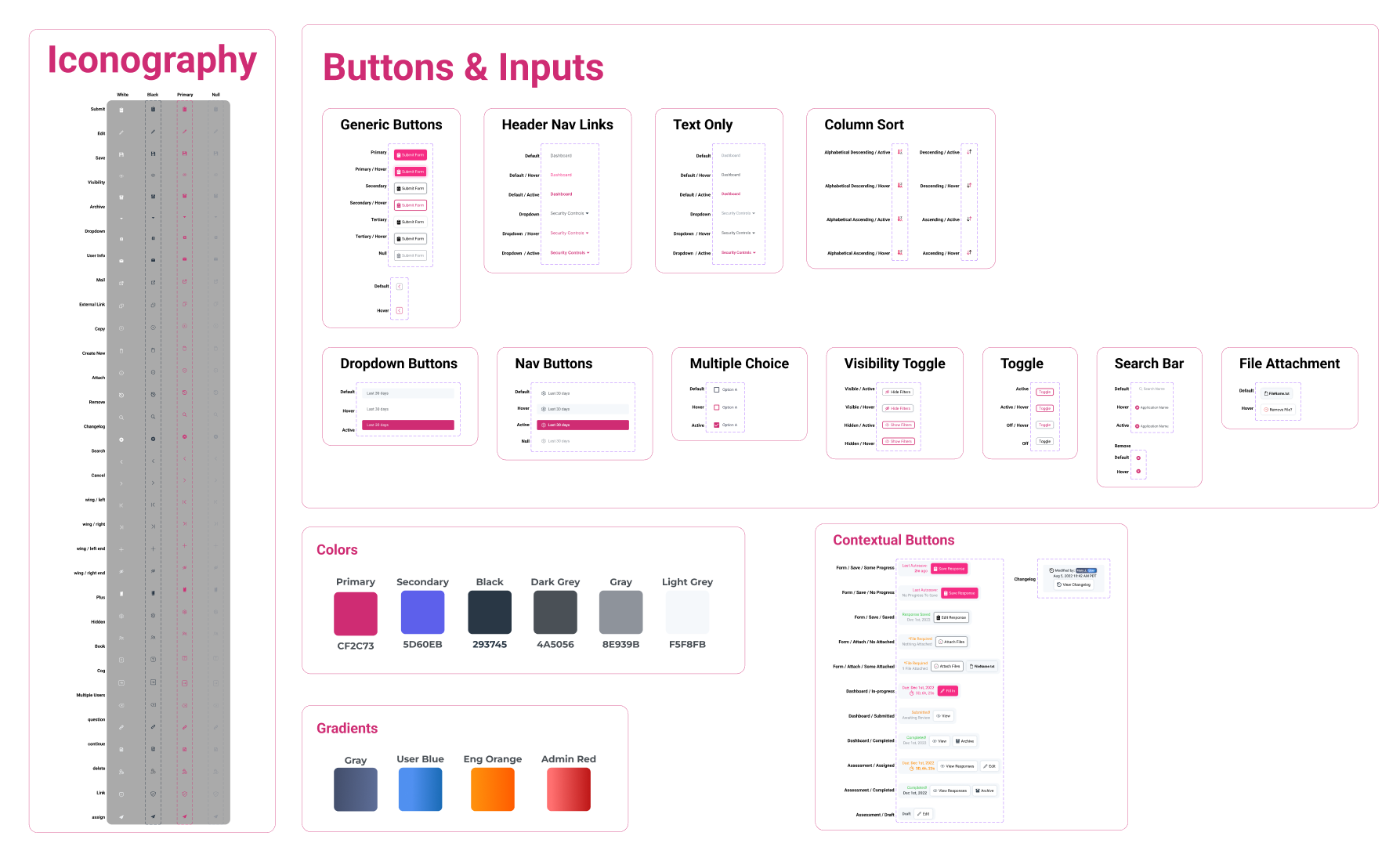
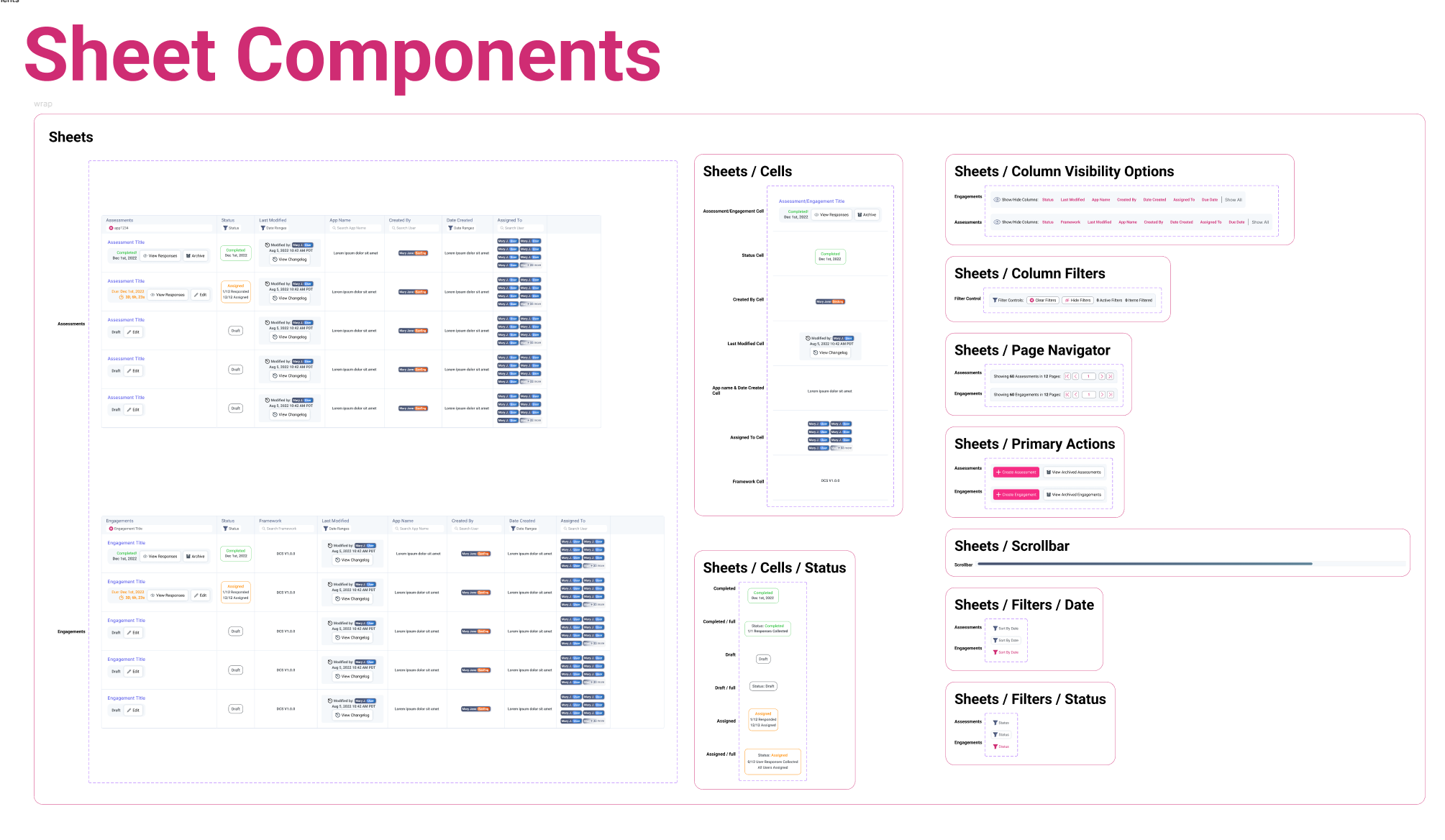
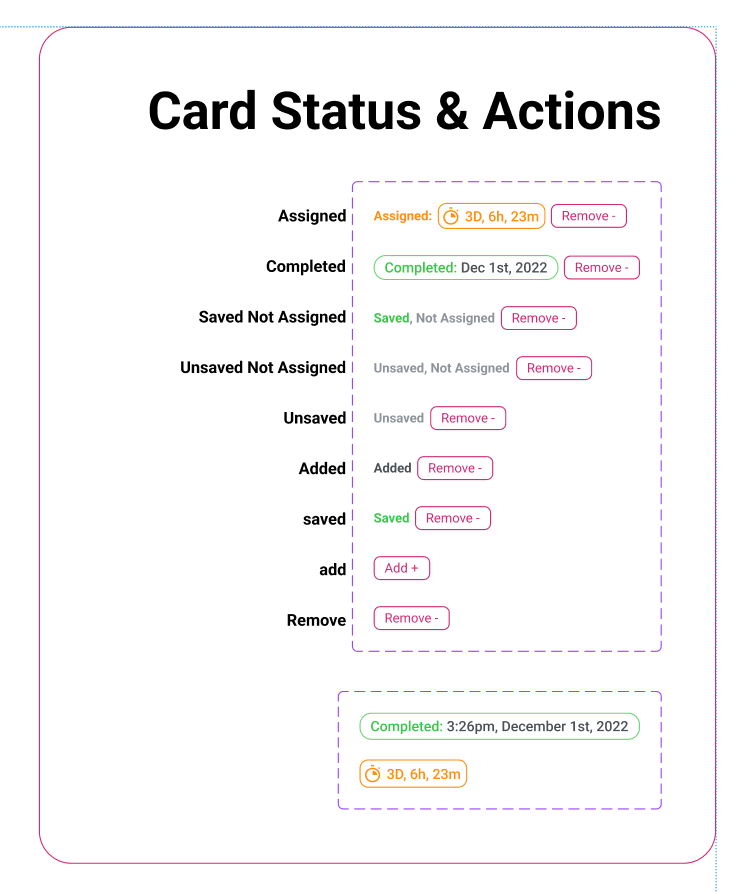
2c. Component Library
Design System
3. User Testing
3. User Testing
That's all for now!
Design Artifacts